On this day, we elaborate on the various steps involved in NIST's(National Institute of Standards and Technology) RMF (Risk Management Framework) and CSF (Cybersecurity Framework).
These are the most popular security and risk-management frameworks that focuses on CIA as discussed in the earlier days. It is used to secure and monitor systems in organizations for potential threats.
In the modern day, we require at least one strong security and one risk-management framework for organisations.
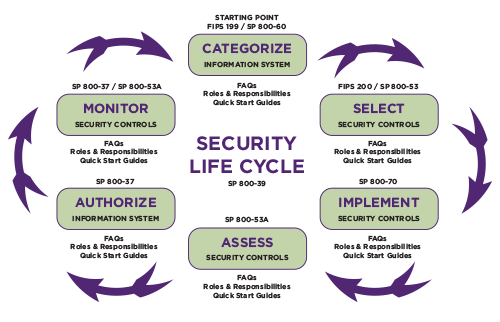
All NIST-RMF steps boiled down
Prepare
Identify the purpose of each kind of system
Identify the types of information and the extent of confidentiality required
Select: Prepare security controls for when dealing with each kind of system
Implement: Implement those security controls
Analyse: Check how well the security controls implemented are working on securing the data
Authorise: Continously report the implemented changes and their impact to the division's senior in the organization and request for their suggestions for improvements
Monitor: Continuously monitor systems for pointing out any issues in compliance or security posture.
All CSF steps boiled down:
Identify
Protect: Implement security controls like setting up encryption to protect organizational assets.
Detect: Investigate any unusual activities and check for unauthorized access.
Respond: Prepare plans for notifying the authority concerned with the risk, Investigating and containing the attack.
Recover: Keep concerned employees informed with the attack and the measures taken to reduce the impact, restore any lost equipment or software.
